If you followed the security recomendations in Office 365 and disabled the ability for users to consent for apps, iPhone users will be facing the message “iOS accounts needs permission to access resources in your organization” during native mail account setup for Exchange Online.
I had this situation and find some articles to solve the problem. I would like to give you a short summary of these articels.
Find your Tenant ID
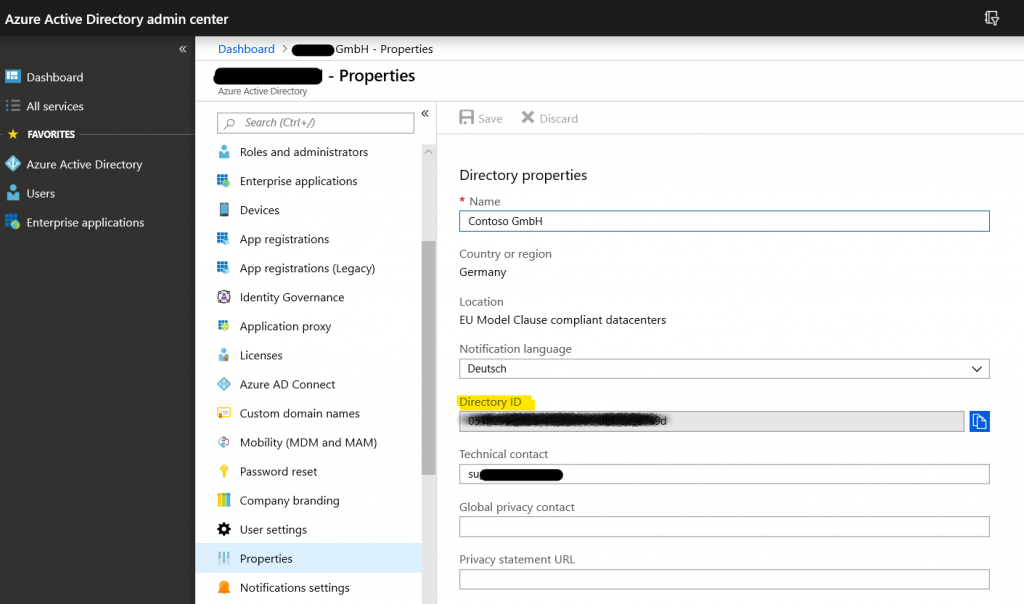
To solve the iOS problem, you need your Office 365 tenant ID first. To get this, open your Azure AD admin center.
Under favorites, switch to the Azure Active Directory category and open the properties of your AAD. On the right site, you will find your Tenant ID. Please copy this ID to your clipboard.
Allow Apple Accounts app in your tenant
Now, you have to modify a URL to allow the Apple accounts app accessing your Office 365 tenant. To do this, the following URL is required
https://login.microsoftonline.com/<TenantID>/oauth2/authorize?client_id=<AppID>&response_type=code&redirect_uri=<RedirectURI>&prompt=admin_consentThe iOS Apple Account AppID is f8d98a96-0999-43f5-8af3-69971c7bb423. An OAuth redirect URL for the Apple iPhone doesn’t exist. A
Next, you will be asked to grant access to your Office 365 Tenant for the iOS Accounts app:
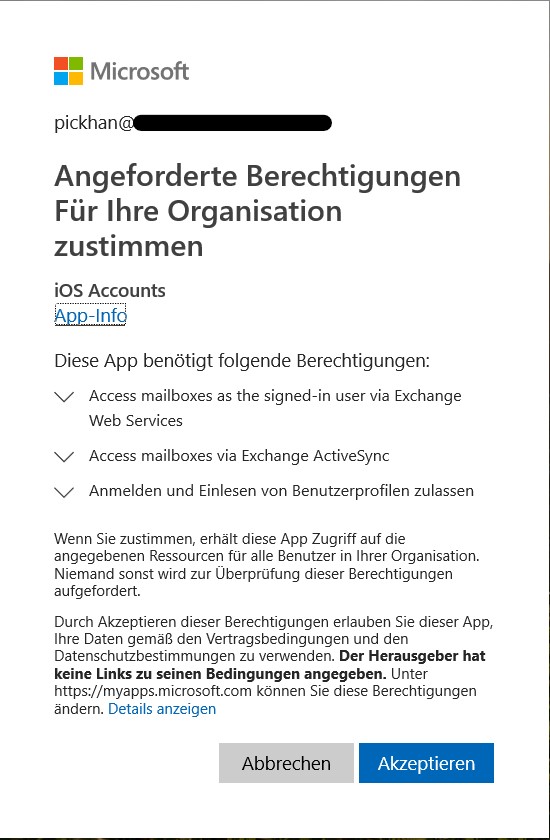
After clicking “Accept”, you will be forwarded to the redirect URL. Windows is asking for an app to open this OAuth file. You can cancel that one. The iOS Accounts app should we registered and your iOS users can set up their phones for Exchange Online without additional prompt.
Check Azure AD for allowed apps
After completing this section, you can check, if iOS Accounts app is approved in your Azure AD. To do this, open again your Azure AD portal and switch on the left to Enterprise Applications.
Here, you will get a list of all registered apps in your Azure AD Tenant. If you succesfully registered iOS Accounts app for your tenant, it should be visible here:
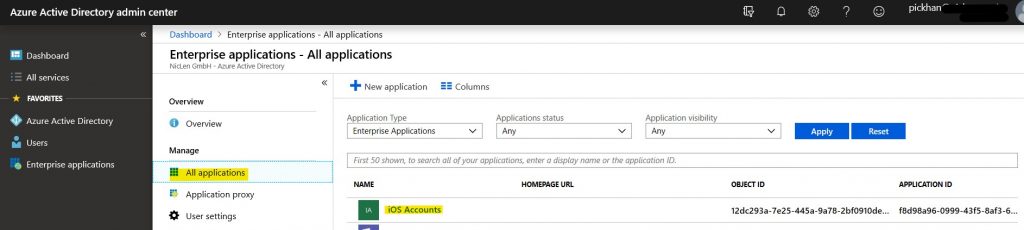
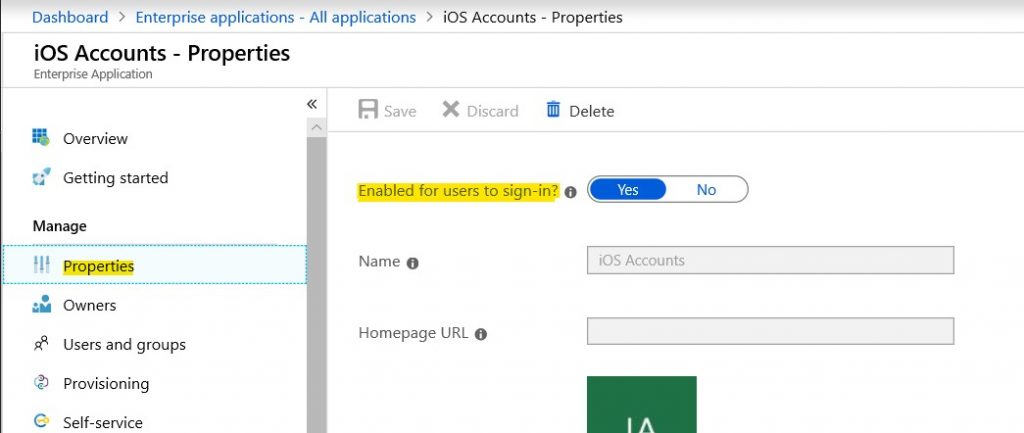
Also you can check the properties of this application and you will see, that the app is allowed to be registered by your Office 365 users.
Why you should think about disabling 3rd party Add-Ins in Office 365
There are some good reason why you should consider to disable access of 3rd party Add-Ins to your Office 365 tenant. One good example you can find here:
Links
- How to get your Tenant ID – by Tom Arbuthnot
- Grant Access to your Tenant – Answer by Mike Crowley
I “think” I have something similar to this. I have am using Microsoft Intune to provide secure MDM and mobile access to our O365 tenant.
In order for DLP to work I want to use application protection policies. However, although I want block third party email apps (incuding iOS native email) I want native iOS contacts and calendar to still function. In your experience, is this possible?
Hi Stoney, thanks for your comment. I’m not sure and therefor can’t answer your question, sorry. I did some searches with Google and found a Microsoft docs article which describes the general app protection policy for iOS and there is a parameter included to enable or disable native contact sync. But I didn’t find an answer what happens, when you generaly block all third party mail app besides Outlook mobile.
https://docs.microsoft.com/en-us/mem/intune/apps/app-protection-policy-settings-ios